Goal :
1. Learn about the conceptual, implementation aspects of network application protocols (Transport-layer service models, client-server paradigm, Peer-to-Peer Paradigm, Content Distribution Networks)
2. Learn about protocols by examining popular application-level protocols (HTTP, FTP, SMTP, POP3, IMAP, DNS)
3. Create Network Applications with Socket API
Chapter 2.1) Principles of Network Applications
Chapter 2.2) Web and HTTP
Chapter 2.3) Electronic Mail
Chapter 2.4) DNS
Chapter 2.5) P2P Applications
Chapter 2.6) Video Streaming and Content Distribution Networks
Chapter 2.7) Socket Programming with UDP and TCP
===
- At the core of network application development is writing programs that run on different end systems and communicate with each other over the network.
- Such examples might be Client-Sever or Peer-to-Peer Paradigms.
- Since Network-core devices(e.g. Routers or Link-layer Switches) do not function at the application layer but instead function at lower layers, therefore as a programmer, we should write software that will run on end systems only.
- From the application developer's perspective, the network architecture is fixed and provides a specific set of services to applications.
Client Server Architecture

- Server is always on host with a permanent IP address.
- Server receives a request for an object from a client host, and it responds by sending the requested object to the client host.
- Clients do not directly communicate with each other, and have dynamic IP addresses.
- Since the server can quickly become overwhelmed if it has only one server handling all of its requests, a data center, hosting a large number of hosts is often used to create a powerful virtual server.
Peer-to-Peer Architecture

- In a P2P architecture, there is minimal or no reliance on dedicated servers in data centers.
- Instead, the application exploits direct communication between pairs of intermittently connected hosts called Peers.
- Because peers communicate without passing through a dedicated server, each peer adds service capacity to the system by distributing files to other peers.
- It is also therefore cost effective, but face challenges of security, performance, and reliability due to highly decentralized structure.
Process Communicating
- Processes are program running within a host, and specifically, we are interested in how processes running on different hosts communicate.
- Processes across two different end systems communicate with each other by exchanging messages across computer networks.
- A process sends messages into, and receives messages from, the network through a software interface called a socket.

- We could view socket as analogous to a door.
- Socket is the interface between the application layer and the transport layer within a host, and is therefore referred to as a the Application Programming Interface(API) bewtween application and the network.
- To recieve messages, process must have an identifier, IP address and port number.
- A port number is needed becauses multiple processes can be running on the same host.

Transport Services Available to Applications
- When developing an application, the developer must choose one of the available transport-layer protocol.
- Protocol is the rules for when and how processes send & respond to messages.
- If protocol provides a guaranteed data delivery service, it is said to provide reliable data transfer.
- If protocol guarantees available throughput at some specific rate, it is called as bandwidth-sensitive application.
- The TCP service model includes a connecteion-oriented service and a reliable data transfer service.
- Connection-oriented service is a handshaking procedure that alerts the client and server, allowing them to prepare for an onslaught of packets.
- TCP also includes a congestion control, a throttle sender when network is overloaded.
- Meanwhile, UDP is a no-frills, lightweight transport preotocol, providing minimal services.
- UDP is connectionless, meaning there is no handshake before two processes start to communicate.
- UDP provides an unreliable data transfer service, and does not include a congestion-control mechanism.
Q1) Why use UDP instead of TCP?
- While UDP is almost an empty protocol, on some applications, TCP's reliable transport is not well fitted, but rather would like to design their own mechanism for reliable transport.
Q2) With TCP and UDP missing any mention of throughput or timing guarantees, can time-sensitive applications such as Interent telephony run in today's Internet?
- These applications often work fairly well because they have been designed to cope, to the greatest extent possible, with the lack of guarantee. Therefore, today's Internet can often provide satisfactory service to time-sensitive applications, but it cannot provide any timing or throughput guarantees.
- TCP and UDP does not provide encryption, so as programmers, we should develop security at Application layer.
- SSL provides encrypted TCP connection.
HTTP Overview
- HyperText Transfer Protocol(HTTP) is the Web's application-layer protocol, and is at the heart of the Web.
- A web page consists of objects, which is a file(HTML file, JPEG image, JAva applet, or a video clip).
- Each object is addressable by URLs.
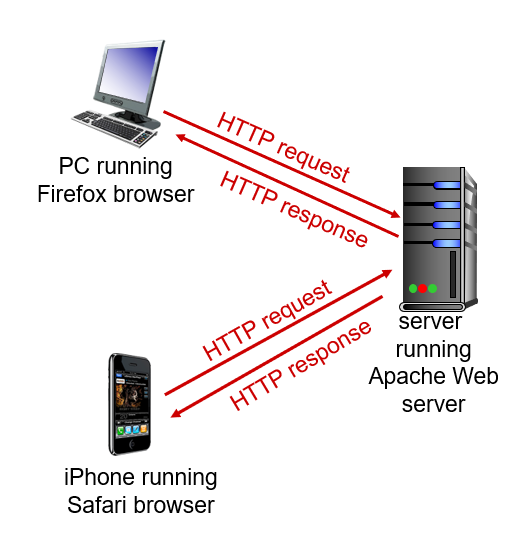
- When a user requests a Web page, the browser sends HTTP request messages for the objects in the page to the server.
- The server receives the requests and responds with HTTP response message that contains the objects.
- HTTP uses TCP as its underlying transport protocol.
- HTTP server maintains no information about the clients, so HTTP is said to be a stateless protocol.
- When each request and response pair is sent over a separate TCP connection, at most one object is sent over TCP connection, and is called non-persistent HTTP.
- When multiple objects can be sent over a single TCP connection between client and server, it is called persistent HTTP.

- Round-trip Time(RTT) is the time it takes for a small packet to travel from client to server and then back to the client.
- RTT includes packet-propagation delays, packet queueing delays in intermediate routers and switches, and packet-processing delays.
- Non-persistent HTTP response time takes 2RTT + file trnasmission time(One RTT to establish the TCP connection and one RTT to request and recieve an object).
- Browsers often open parallel TCP connections to fetch referenced objects.
- Persistent HTTP response takes 1RTT for all the referenced objects.

- In kernal level, binary format messages are used, but in HTTP, ASCII format is used.
- Some examples of HTTP request message are POST, GET(URL included), HEAD, PUT.
- Some examples of HTTP response message is 200, 301, 400, 404, 505.
Cookies
- Since HTTP server is stateless, HTTP ues cookies.
- Purpose of cookes are to restrict user access or serve content as a function of the user identity.
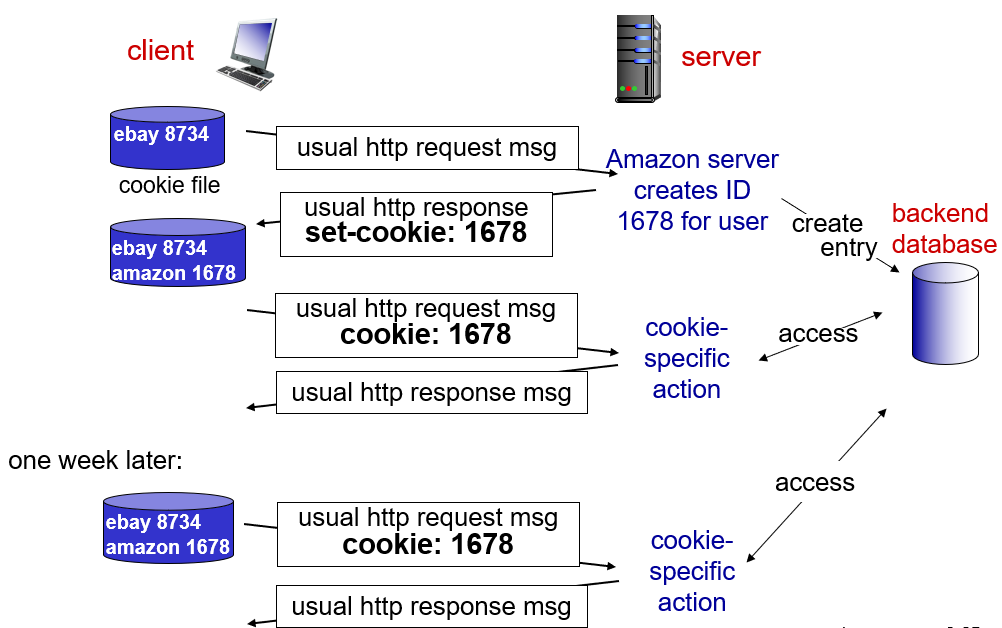
- When there is a transaction, the client sends message with the recieved cookie.
- Cookies have downside because they can also be considered as an invasion of privacy.
Web Caches (Proxy Server)
- Web Caches(Proxy Server) is a network entity that satisfies HTTP requests on the behalf of an origin Web server.
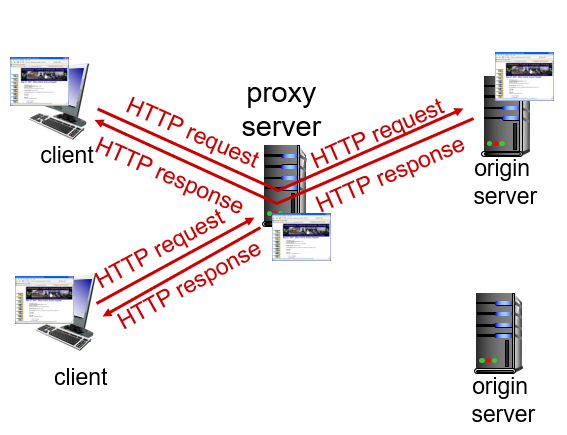
- Setting a proxy server, the client requests to the Web cache, and if it has a copy, it sends back, and if not, it requests to the server, stores a copy, and send back to the client.
- Web caches is purcahsed and installed by an ISP such as university.
- The advantages of Web cache is that it can substantially reduce the response time for client request, and it can substantially reduce traffic on an institution's access link to the Internet.
Case Study 1) Electronic Mail
- The 3 major components of Electronic Mail are user agents, mail servers, and simple mail transfer protocol(SMTP).
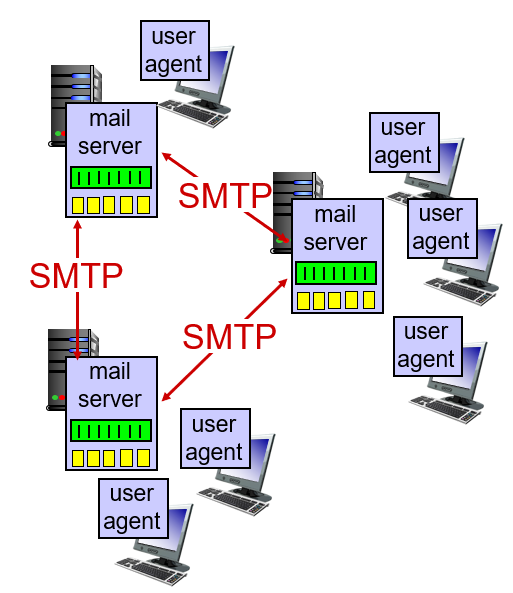
- User Agents(Mail Reader) compose, edit, and read mail messages.
- Mail Servers consists of mailbox containing incoming messages for user.
- Simple Mail Transfer Protocol(SMTP) is the standard protocol bertween mail servers to send email messages.
- SMTP transfer messages from senders' mail servers to recipients' mail server.
- SMTP uses TCP to reliably transfer email message from client to server, using port 25.
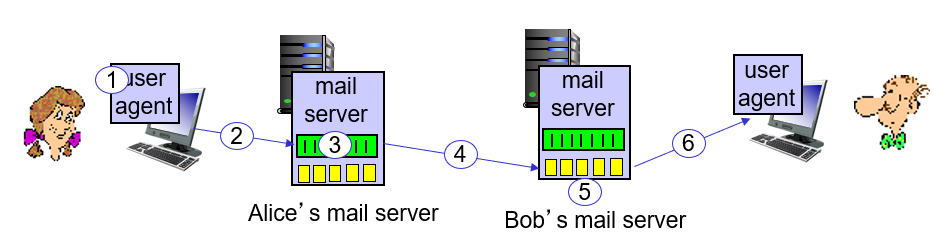
- SMTP restrict the body(not just the headers) of all mail messages to simple 7-bit ASCII because in the early 1980s, tramission capacity was scarce.
- SMTP consists of 3 phases of transfer, handshaking, transfer of messages, and closure.
- Like HTTP, SMTP uses persistent connections.
- Different from HTTP, while HTTP is mainly a pull protocol, SMTP is primarily a push protocol.
- Also, while HTTP encapsulates each object in its own HTTP response message, SMTP places all of the message's objects into one message.
- RFC 822 is the standard for text message format.

- RFC 822 is consisted of header lines and the body(message).
- 3 Access Protocols for retrieving messages from mail server are POP, IMAP, HTTP.
- POP3 is consisted of authorization phase and transaction phase.
- POP3 is designed to download-and-keep, but IMAP is designed to keep messages in server.
Case Study 2) DNS : Domain Name System
- Like human, computers have multiple forms of identifiers.
- One identifier for host is its hostname.
- Hostnames consist of variable-length alphanumeric characters, so it would be difficult to process by routers, therefore they use IP addresses.
- Domain Name System(DNS) is a directory service that translates hostnames to IP addresses.
- DNS is commonly employed by other application-layer protocols including HTTP and SMTP to translate user-supplied hostnames to IP addresses.
- Because centralized database in a single DNS server doesn't scale, the DNS uses a large number of servers, organized in a hierarchical fashion and distributed around the world.
- No single DNS server has all of the mappings for all of the hosts in the Internet, but are distributed across the DNS servers.

- The 1st approximation is for the client to contact one of the root servers, which returns IP addresses for Top-Level Domain(TLD) Servers for the top-level domain.
- The client then contacts one of these TLD servers, which returns the IP address of an authoritative server.
- Finally, the client contacts one of the authoritative servers.
- The root, TLD, and authoritative DNS servers all belong to the hierarchy of DNS servers.
- One other type of server is local DNS server.
- Local DNS Server does not strictly belong to the hierarchy of servers but is nevertheless central to the DNS architecture.
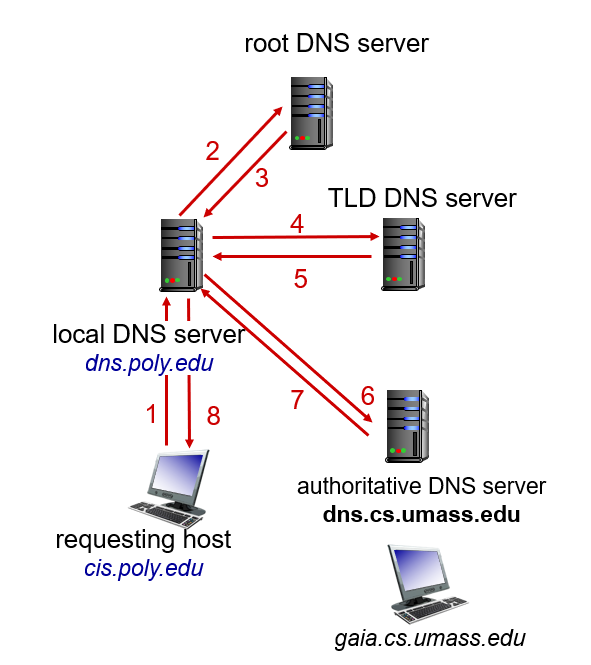
- Such ISP(residential, company, university) has a local DNS server, and when the host connects to an ISP, the ISP provides the host with the IP addresses of one or more of its local DNS servers.
- The figure above is an example of iterated query.
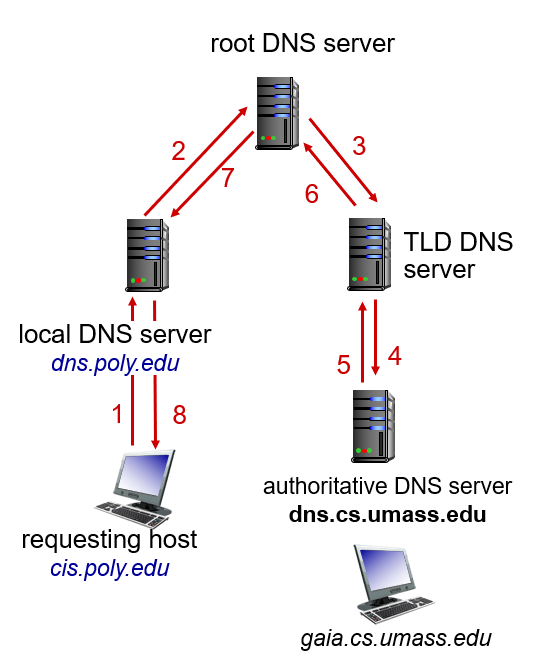
- An alternative is recursive query, but is not recommended becuase root DNS is overloaded.
- Once any name server learns mapping, it caches mapping.
- Cache entries timeout after some time.
- TLD servers typically cache in local name servers, thus root name servers are not often visited.
- Cached entries may be out-of-date.

- DNS servers that implement the DNS distributed database store resource record(RR).
- RR contains a name and a value depending on type.
- For type A, name is hostname, and value is IP address.
- For type NS(Name Server), name is domain, and value is hostname or authoritative name server for this domain.
- For type CNAME, name is alias name, and value is canonical name.
- For type MX, value is name of mailserver associated with name.
- To register a domain name, one should provide names, IP addresses of authoritative name server, and DNS registrar will insert two RRs into .com TLD server.
'Network' 카테고리의 다른 글
| Transport Layer (3/3) (0) | 2021.10.12 |
|---|---|
| Transport Layer (2/3) (0) | 2021.10.11 |
| Transport Layer (1/3) (0) | 2021.10.11 |
| Application Layer (3/3) (0) | 2021.10.11 |
| Application Layer (2/3) (0) | 2021.09.27 |



